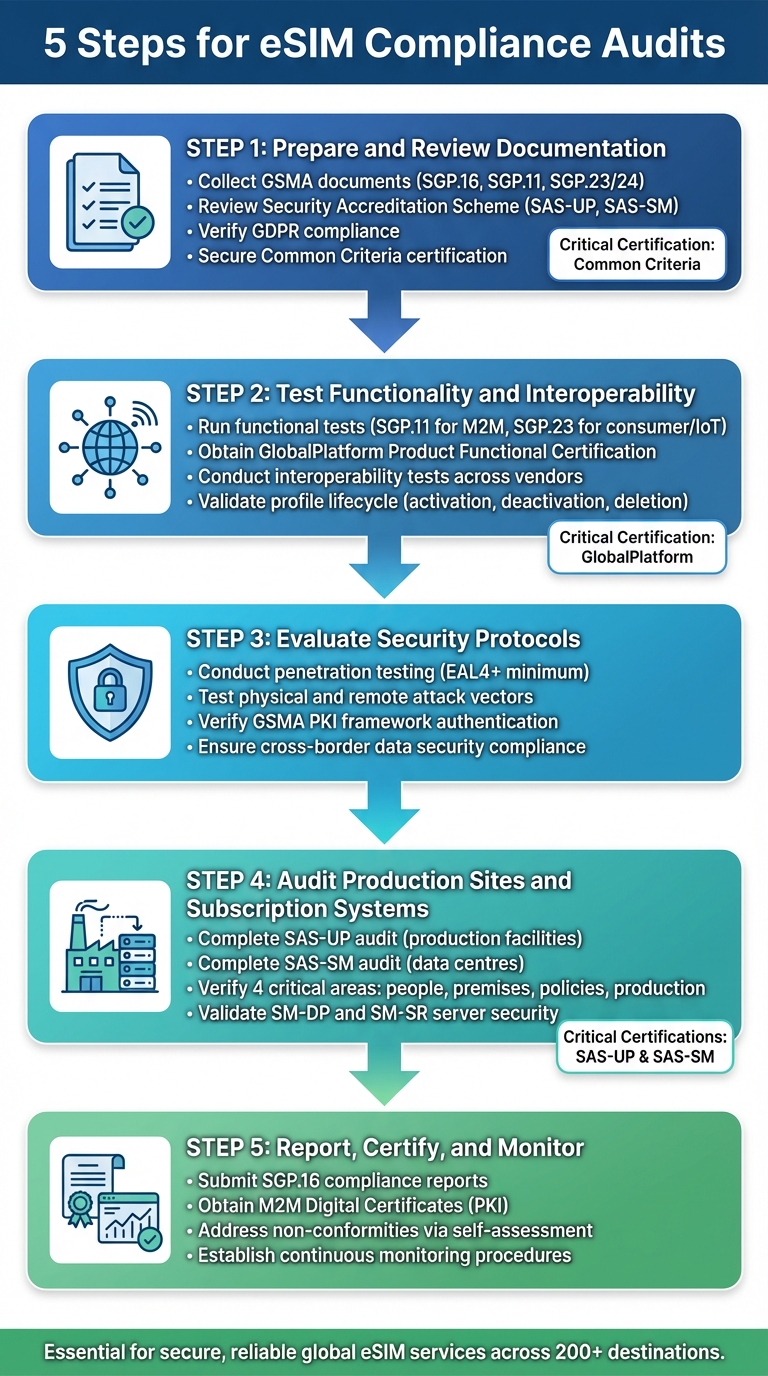
5 Steps for eSIM Compliance Audits
https://www.zimconnections.com/5-steps-for-esim-compliance-audits/
 SHARE
SHARE
eSIM compliance audits ensure that eUICCs and subscription management servers meet GSMA‘s technical, functional, and security standards. These audits are vital for global eSIM functionality, security, and interoperability. Here’s a quick overview of the five steps to achieve compliance:
- Prepare and Review Documentation: Collect essential GSMA documents (e.g., SGP.16, SGP.11) and review data privacy policies for regional and global requirements like GDPR.
- Test Functionality and Interoperability: Conduct functional tests (SGP.11, SGP.23) and interoperability tests to ensure smooth operations across devices and networks.
- Evaluate Security Protocols: Perform penetration testing, verify hardware certifications (e.g., Common Criteria), and ensure secure cross-border data handling.
- Audit Production Sites and Subscription Systems: Follow GSMA’s SAS-UP and SAS-SM frameworks to secure manufacturing facilities and subscription management systems.
- Report, Certify, and Monitor: Submit audit reports, address non-conformities, and establish continuous monitoring to maintain compliance.
These steps ensure secure, reliable, and compliant global eSIM services. For businesses like ZIM Connections, adhering to these standards is critical for providing secure international connectivity.
5 Steps for eSIM Compliance Audits Process Flow
How To Audit Third-Party Data Processors For Compliance?
Step 1: Prepare and Review Documentation
Start by gathering all the necessary documentation and ensuring that your data privacy policies align with cross-border regulations. This step is crucial for conducting a seamless audit, especially when managing eSIM services like ZIM Connections’ international plans, which span over 200 destinations. Once this groundwork is in place, move on to collecting the required compliance documents.
Collect Required Compliance Documents
Begin by downloading essential documents directly from the GSMA website. These include:
- SGP.16: Contains the compliance requirements and declaration templates.
- SGP.11: Details functional and interoperability test cases forming the compliance baseline.
- SGP.23/SGP.24: Provide QR code specifications and RSP process definitions.
Next, review the Security Accreditation Scheme (SAS) documents. These audits ensure secure handling of sensitive assets like MNO profiles and PKI certificates:
- SAS-UP: Focuses on auditing production sites where eUICCs are manufactured.
- SAS-SM: Evaluates subscription management service locations.
Keep in mind that these audits require careful scheduling, so factor in lead times when planning your compliance timeline.
Your eUICC hardware must also meet stringent security standards through Common Criteria certification, adhering to Protection Profiles such as PP-0084, PP-0117, or SGP.25. Additionally, securing GlobalPlatform Product Functional Certification is a mandatory step before declaring SGP.16 compliance. If you need to update software on certified products, you can request the self-assessment procedure by emailing M2Mcompliance@gsma.com.
Here’s a quick reference table for the key documents and their purposes:
| Document | Purpose | Target Entity |
|---|---|---|
| SGP.16 | Compliance requirements and declaration templates | eUICC & SM Servers |
| SGP.11 | Functional and interoperability test cases | M2M Systems |
| SGP.23 | Test specifications for QR codes and requirements | Consumer/IoT eSIM |
| SGP.24 | RSP compliance process definitions | RSP Ecosystem |
| SAS-UP | Security audit for production and data handling | eUICC Manufacturers |
| SAS-SM | Security audit for subscription management locations | SM-DP / SM-SR |
Review Data Privacy Policies
Once the compliance documents are in order, turn your attention to reviewing your data privacy policies. This involves verifying GDPR compliance and ensuring adherence to regional regulations for cross-border data transfers. For ZIM Connections’ regional plans, such as those covering multiple European countries, you’ll need to account for EU-area eUICC certification scheme requirements.
On the other hand, global plans – spanning 125 countries across four continents – demand a more detailed review. Subscription management developers must demonstrate secure handling of MNO profile data and digital certificates across various jurisdictions.
The audit complexity increases with the scope of the plan:
- Local plans (single-country coverage): Focus on data residency and MNO-specific security protocols.
- Regional plans: Must comply with frameworks like GDPR.
- Global plans: Require robust SAS-SM audits for data centres managing worldwide connectivity.
For ZIM users travelling internationally, their eSIM connects to local networks while maintaining default data line settings. This makes verifying cross-border data security a critical part of the audit preparation process.
Step 2: Test Functionality and Interoperability
Once your compliance documentation is in order, the next step is to ensure your eSIM performs flawlessly across various devices and networks. Functional and interoperability testing is essential to confirm that profiles can be downloaded, activated, and removed without any technical issues. This step is crucial for maintaining seamless connectivity across different regions.
Run Functional Tests
Functional testing checks whether all system interfaces work as they should, following GSMA specifications. For this, you’ll rely on standards like SGP.11 for M2M applications and SGP.23 for consumer and IoT use cases. These tests ensure that your eUICC communicates effectively with Subscription Management servers.
To add another layer of assurance, seek GlobalPlatform Product Functional Certification. This certification verifies that your eSIM profiles function correctly across different vendors. For example, with ZIM Connections’ 5G/4G plans, functional testing ensures that profile data is formatted and recognised across various regional frequency bands.
You can use commercial test suites aligned with SGP.11 or SGP.23 to verify the robustness of eUICC communication and interfaces. Alternatively, mobile network operator (MNO)-based testing can be an option, provided all SGP.11 scenarios are thoroughly covered. These tests should address the entire lifecycle of an eSIM profile, including remote activation, deactivation, and deletion, ensuring dependable service delivery.
"The GSMA M2M test specification, SGP.11, provides functional and interoperability test cases for M2M system operation. It is the basis for M2M testing for functional compliance and interoperability." – GSMA
Once functionality is confirmed, move on to interoperability testing to ensure smooth operation across different vendors and platforms.
Run Interoperability Tests
Interoperability testing ensures that an eSIM profile from one provider can be provisioned and managed on devices from various manufacturers. This guarantees vendor independence and global compatibility, which is especially important as eSIM adoption grows worldwide.
GlobalPlatform-qualified testing labs are equipped to carry out standardised test plans, ensuring your eUICC operates seamlessly across a wide range of devices. Additionally, take into account any specific regional requirements or mandates that might apply.
As deployments scale, interoperability testing becomes more complex. It must cover a variety of use cases to confirm compatibility across different vendor systems and deployment scenarios.
"The lack of standardisation creates risks of interoperability issues that lead to extra costs and complications when deploying and managing IoT devices." – Baruch Pinto, Webbing Solutions
Using the latest GSMA specifications, validate your compliance evidence to ensure smooth operation. For ZIM Connections, which operates in over 200 destinations, thorough interoperability testing ensures users can effortlessly connect to local networks while maintaining secure cross-border data transfers. These tests are the final step in the validation process, ensuring your eSIM service meets the high standards required for reliable global connectivity.
Step 3: Evaluate Security Protocols
Once functionality tests are complete, it’s time to assess the security measures safeguarding sensitive eSIM data, especially within various regulatory frameworks. The GSMA SGP.05 standard provides a strong foundation for eUICC security by requiring all M2M-compatible eUICCs to withstand high-level attack scenarios. Compliance can be demonstrated through certifications like Common Criteria PP-0089 or GSMA eSA (eUICC Security Assurance), with the hardware meeting relevant Common Criteria standards. These certifications ensure that user data remains protected, even during international data transfers. This step bridges the gap between functional testing and the rigorous security checks necessary for global operations.
Conduct Penetration Testing
Start by identifying vulnerabilities before they can be exploited, building on the secure operations already established. The Remote SIM Provisioning specification mandates an Evaluation Assurance Level of at least EAL4+ for eUICC certification. Pay close attention to the Java Card Virtual Machine, as vulnerabilities – such as "type confusion" – could allow attackers to bypass security measures and extract private ECC keys.
One notable example involved Security Explorations compromising a Kigen eUICC card by installing a malicious applet via the OTA SMS-PP protocol. This breach led to the extraction of private ECC keys and the downloading of decrypted eSIM profiles from major operators like AT&T, Vodafone, and T-Mobile. The vulnerability prompted Kigen to issue patches for its ECu10.13 product and collaborate with the GSMA to update the TS.48 Generic Test Profile specification.
"The level of detail in your findings has been incredibly helpful – your work has played a crucial role in enabling us to fully understand the issue and begin crafting effective mitigation strategies."
– Kigen Representative, Response to Security Explorations
Testing should include both physical and remote attack vectors. For physical access, side-channel attacks are a key concern, while remote testing should scrutinise the SMS‑PP protocol during applet installations. Enforce strict type safety checks for Java Card bytecode instructions and disable test profile applets in line with GSMA TS.48 v7 guidelines to address chain-of-trust vulnerabilities.
After identifying and addressing vulnerabilities, shift the focus to ensuring secure data transfers across borders.
Verify Cross-Border Data Security
Cross-border data security is crucial for maintaining eSIM profile integrity as users move between different regions. For example, ZIM Connections’ global plans, spanning 125 countries, rely on secure transitions between local networks. Subscription Management audits (SAS‑SM) are essential, ensuring that SM‑DP and SM‑SR servers implement stringent security controls. Authentication is handled through the GSMA PKI framework, which provides secure digital certificates for communication between servers and devices. Only certified eUICCs and Subscription Management servers should exchange sensitive data. Additionally, confirm that the eUICC OS update mechanism prevents unauthorised firmware modifications, whether over-the-air or via physical access. Regular SAS‑SM audits are vital for maintaining compliance as your service expands, supporting GDPR and other regional regulations outlined in Step 1. These measures uphold the high-security standards expected by travellers and businesses relying on ZIM Connections for seamless global connectivity.
| Security Component | Standard/Requirement | Purpose |
|---|---|---|
| eUICC Security | GSMA SGP.05 | Resists advanced hardware/software attacks |
| Hardware Platform | PP-0084 / PP-0117 | Ensures baseline Common Criteria protection for the chip |
| Data Management | SAS‑SM | Protects user data and MNO profiles during international transfers |
| Authentication | GSMA PKI (SGP.14) | Secures server-to-device communication with digital certificates |
sbb-itb-273ea09
Step 4: Audit Production Sites and Subscription Systems
Once security protocols are verified, the next step is to examine the facilities and systems responsible for manufacturing and managing eSIMs. The GSMA’s Security Accreditation Scheme (SAS) provides a structured framework for these audits, focusing on both the production sites (SAS-UP) and the data centres that host subscription management servers (SAS-SM). As the industry standard, SAS is widely adopted by over 100 leading UICC/eUICC and subscription management suppliers, ensuring secure eSIM operations are maintained across the board. With security and interoperability documented, auditing both the physical and digital systems becomes a crucial step.
Audit Production Sites (SAS-UP)
The Security Accreditation Scheme for UICC Production (SAS-UP) is designed to audit the physical locations where eUICCs are manufactured. GSMA auditors independently assess four critical areas: people, premises, policies, and production processes. These audits ensure that critical assets are securely managed throughout the manufacturing workflow.
Before scheduling an audit, confirm that the eUICC hardware has the necessary Common Criteria certification (PP-0084, PP-0117, or PP-0035), as this is a prerequisite for SAS-UP compliance. It’s also important to plan audit timelines carefully, as they require preparation. For added convenience, GSMA maintains a continuously updated online list of accredited suppliers, enabling operators to make informed decisions without needing to conduct their own audits. After addressing production site security, the next focus should be on subscription management systems.
Audit Subscription Management Systems (SAS-SM)
Building on the secure protocols established earlier, SAS-SM audits focus on the security of data centres and hosting locations that operate SM-DP (Subscription Management Data Preparation) and SM-SR (Subscription Management Secure Routing) servers. Independent auditors ensure that subscriber profiles are securely managed and that all functional interfaces comply with SGP.11 test specifications.
For global plans, such as those offered by ZIM Connections, SAS-SM certification guarantees consistent security measures across all locations. Once SAS-SM accreditation is achieved, a declaration of compliance (SGP.16) can be submitted to the GSMA. This step is essential for obtaining M2M Digital Certificates (PKI), which enable secure authentication between eUICCs and subscription management servers. Regularly renewing the accreditation ensures that compliance is maintained as operations expand.
| Audit Type | Target Entity | Focus Area | Key Components |
|---|---|---|---|
| SAS-UP | eUICC Manufacturers | Production facilities | Physical security, manufacturing data handling, personnel policies |
| SAS-SM | Subscription Management Providers | Data centres and hosting locations | SM-DP, SM-SR, secure profile management, digital infrastructure |
Step 5: Report, Certify, and Monitor
Once you’ve completed the audits of production sites and subscription systems, the next step is to translate those findings into compliance certifications and set up a system for ongoing monitoring. This ensures that your operations not only meet current standards but continue to align with them as they evolve.
Prepare and Submit Audit Reports
Your audit reports need to follow the GSMA PRD SGP.16 templates. These reports are essential for demonstrating compliance with M2M remote provisioning standards (SGP.01 and SGP.02). Make sure to include:
- Certificate references
- Hardware certification evidence
- Proof of SAS-UP and SAS-SM audits
- GlobalPlatform Product Functional Certification for eUICCs
- Verification that all SM-DP and SM-SR interfaces have been tested using SGP.11 test scenarios
For any product updates, clearly state the "Declared build" version, the date of the change, and details of any software modifications. Once submitted, a successful SGP.16 declaration of compliance not only marks a major milestone but also makes you eligible for M2M Digital Certificates (PKI), which are key for secure authentication between eUICCs and subscription management servers.
"The result of a successful SGP.16 declaration of compliance is a recognised achievement plus eligibility to use an M2M Digital Certificate (PKI)".
Fix Non-Conformities
If your audit reveals any gaps, these need to be addressed promptly. Use the GSMA Self-assessment procedure to document and resolve non-conformities. To begin, request the self-assessment document by emailing M2MCompliance@gsma.com. Fill it out with details of the changes made and submit it to the GSMA RSP Compliance Team for review. They will determine if the modifications affect RSP, SAS, or TOE (Target of Evaluation) features.
For subscription management systems, all interfaces should be verified using commercial SGP.11 test suites or through interoperability testing with mobile network operators (MNOs). Any security issues at production sites or service locations must be resolved through the SAS audit process. Once all non-conformities have been addressed, you’ll receive an updated "GSMA Confirmation of PKI Certificate Issuance", which will reflect the new declared build version and certificate issuance date.
After resolving these issues, you can move forward with implementing continuous monitoring to maintain compliance.
Set Up Continuous Monitoring
Establish internal procedures that align with the GSMA Self-assessment process to notify GSMA of any software updates. This ensures that all changes are logged in both the GSMA internal database and the IC2 database, creating a transparent compliance record. Plan SAS-UP and SAS-SM audits well in advance, keeping in mind that "SAS is an audit based scheme, and audit lead time should be considered when planning compliance".
For global operations, such as those managed by ZIM Connections, continuous monitoring is crucial for maintaining security across all locations, especially as operations expand internationally. Keep an eye on PKI certificate revision numbers to ensure they remain valid after updates. Regularly review updates to specifications like SGP.16, SGP.24, and SGP.32. For instance, SGP.24 was revised to versions 2.6 and 3.2 on 27 January 2025, so staying current with these updates is essential to ensure that your testing and certification processes meet the latest requirements.
Conclusion
eSIM compliance audits are more than just ticking boxes – they lay the groundwork for secure and reliable global connectivity. By combining detailed documentation reviews, functional and security testing, facility checks, and ongoing monitoring, providers create systems that can handle the demands of international travellers. Together, these measures form a strong compliance framework essential for seamless global operations.
For companies like ZIM Connections, thorough compliance audits are vital to delivering uninterrupted international connectivity. The GSMA Security Accreditation Scheme (SAS-SM) plays a key role by evaluating the security of data management processes at Subscription Management service locations such as data centres. This ensures that every step, from downloading profiles to authenticating on networks, is carried out securely. Without such compliance, travellers could face connectivity issues or, worse, security risks that might expose their sensitive data.
With the UK Data (Use and Access) Act coming into effect on 19 June 2025, alongside regular updates to specifications like SGP.24 (most recently revised to version 3.2 on 27 January 2025), staying compliant requires constant vigilance. Adapting to these evolving standards is critical to maintaining the integrity of eSIM services. As Srdjan Gombar, a seasoned content writer at CM Alliance, aptly puts it:
"This is a never-ending process that includes regular security audits and vulnerability assessments".
FAQs
Which GSMA documents are essential for ensuring eSIM compliance?
To meet eSIM compliance, several essential GSMA documents come into play. These include the eUICC Security Assurance scheme specifications (SGP.06 and SGP.07), protection-profile specifications (SGP.05 for M2M and SGP.25 for consumer/IoT), and the remote-provisioning architecture and technical specifications (SGP.01 and SGP.02). On top of that, the M2M compliance PRD (SGP.16), baseline security controls (FS.31), and Security Accreditation Scheme guidelines (FS.18) are equally important.
These documents provide a detailed framework of technical and security standards needed to manage eSIMs effectively. They ensure devices comply with global requirements, supporting secure and reliable cross-border connectivity.
What are interoperability tests, and how do they ensure eSIMs work across different devices?
Interoperability tests play a crucial role in verifying that an eSIM works smoothly across different devices and networks. These tests adhere to established standards like ETSI TS 102 901 and GSMA compliance guidelines, focusing on key aspects such as profile activation, secure communication, and compatibility with network infrastructure.
By confirming that an eSIM can exchange data securely and interact effectively with SM-DP/SM-SR systems and device hardware, these tests ensure dependable performance across a variety of devices. This reliability is vital for both individual users and businesses that depend on uninterrupted connectivity.
Why is ongoing monitoring essential after achieving eSIM compliance?
Continuous monitoring plays a key role in keeping your eSIM systems secure, operational, and aligned with GSMA standards over time. It allows for the swift detection and resolution of security gaps, performance issues, or emerging threats.
By staying vigilant, organisations can ensure ongoing compliance, adjust to changing regulations, and maintain smooth cross-border connectivity for their users.









































































































































































































